Say hello to iJihad – Murtaza Haider
Not to be outdone by the rest in the Internet age, the Jihadists have readily embraced modern communication technologies. From their recruitment videos on YouTube to timely tweets of their vicious attacks on civilians, the Jihadists are out and about preaching online to whoever is willing to listen to their diatribe.
It started earlier with the video recorders, when the militants recorded their attacks and sent the videos to the news media. Hezbollah of Lebanon was among the first to use videos of their attacks as a propaganda tool. The advent of YouTube made the task even simpler: kill, record, and upload.
The emergence of Web 2.0 technologies has transformed the way individuals, corporations, and governments communicate, using social media. The jihadists of today are unlike those of yesteryears who shunned all things western.
To the older generations, TV was an evil box. To the modern-day Jihadists, Facebook and Twitter are godsend. Even IS has launched an Arabic language Twitter app (The Dawn of Glad Tidings) to recruit and raise funds.
The Jihadists do share common traits with others in the way they use the Internet to recruit. They use social media to communicate with like-minded individuals and keep them abreast of their activities. Tweeting about their latest exploits or Facebook status updates about attacks in the semi-rural hinterlands of hard-to-reach places, which are yet to be profiled by Google street maps, keep the propaganda engine churning.
However, that’s where the similarities end.
The Jihadists rely on the word-of-mouth approach by placing their content in cyberspace. They have not been able to take out online Ads to target their message at the intended. It is highly unlikely that Google Ads will carry messages for IS or Boko Haram. Instead, the reverse is true. Jihadists social media accounts are routinely suspended by the companies and ISP providers refuse to host their online content. The Jihadists then have learned to operate within the limits to avoid a clampdown on their recognised Internet outlets.
From Alim online to Mujahid online
TV evangelism morphed earlier into digital evangelism. The Jihadists have taken this a step further. They use the social media to field questions from wannabe jihadists.
A European Jihadi wannabe asked an Internet-savvy Jihadist about the quality of dental care in Syria. The aspiring Jihadi was concerned about his braces. Another inquired about the general quality of healthcare. Yet another westerner was concerned about the availability of central heating in Syria and Iraq.
While the Jihadist’s use of social media often provides comic relief, it is also successful in converting young westerners to extremist ideologies. The Great Recession of 2007/08 had a devastating impact on European economies. The youth unemployment rate spiked as a result.
Unemployed rebels without a cause think they can find a purpose in the battlefields of Syria and Iraq. Even young western women are lured by the Jihadist videos some of whom have left for the Middle East to become Jihadi wives.
Better online than offline
Many view the Jihadists use of the Internet to communicate and propagate as a blatant abuse of the public good, the Internet.
Some call for strict restrictions on the Jihadists’ online activities. The Jihadist propaganda invokes centuries-old imagery and reminisces about establishing a caliphate, returning to a barter economy with gold reserves, and uses swords and knives for beheadings.
Given their nostalgic outlook on life and values, many find it odd that the Jihadists have so eagerly adopted the modern ways of communication and warfare. The Internet, automatic weapons, dual cabin vehicles are all products of modern society, which the Jihadists violently oppose and yet, willingly adopt its products at the same time.
The call to push Jihadists off the information highway is understandable, but not useful. The fact that the Jihadists use mobile phones and Internet technologies is extremely helpful in tracking and monitoring their activities.
Given that only a handful of super highways exist through which all digital communications passes, it is quite possible to put in place surveillance systems to monitor chatter and apply filters to the noisy data to determine what is being said or planned.
Most breakthroughs in capturing or terminating violent militants happened either by sheer luck or by effective monitoring of digital communications.
While sophisticated algorithms and access to main Internet switches, through which the digital communications pass through, will be highly useful, still anyone with an Internet connection can peek into what is happening in the Jihadi blogosphere.
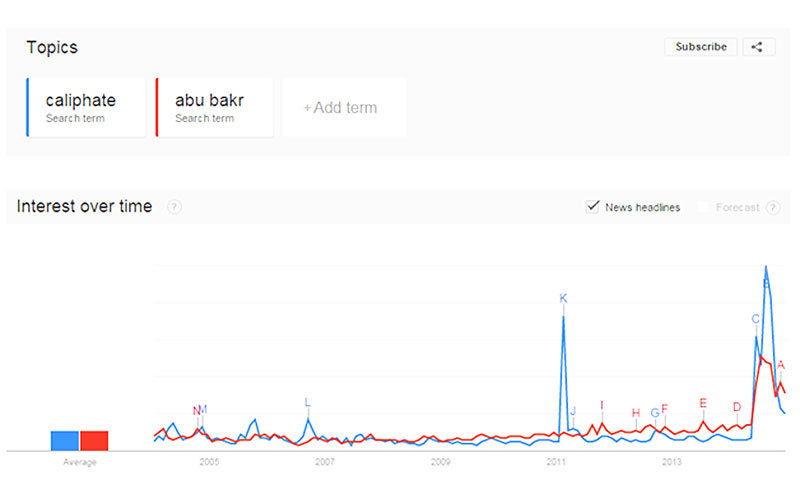
The recent rise of IS and its leader Abu Bakr al-Baghdadi, who fancies expensive watches, can be tracked over time by monitoring the Google searches using Google trends. While Abu Bakr al-Baghdadi surfaced only recently, the Google-based searches for ‘caliphate’ peaked earlier in February 2011.
Globally, Nigeria and Pakistan are the two places where the search for ‘caliphate’ represents the highest share of the Google searches.
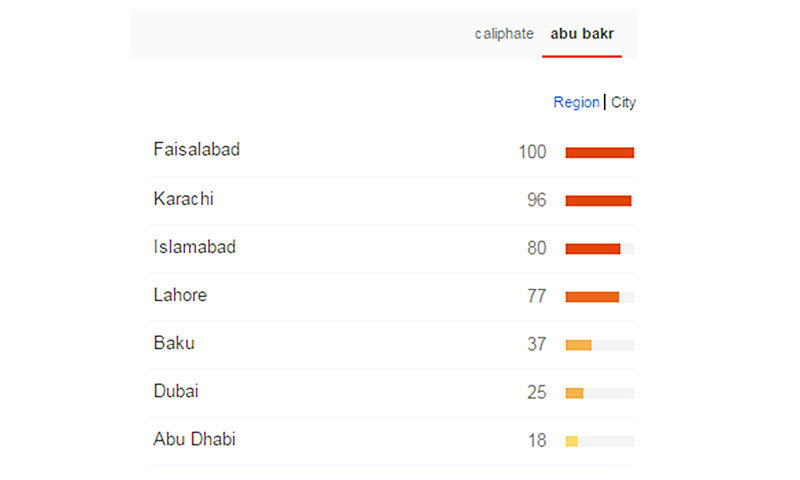
Pakistan ranks at the top for searches for ‘abu bakr’. Within Pakistan, Faisalabad reported the highest concentration of searches for “abu bakr.”
Imagine the kind of intelligence one can collect if the same searches are conducted by individual IP addresses and then aggregated over time and space to determine the contexts in which various dialogues and exchanges take place on social media.
The academics specialising in privacy will be mortified to read these arguments. The challenge, in fact is to balance the need for intelligence against the individual’s right to privacy. It is easier said than done, especially when the militant Jihadists do not play by any rulebook.
In the not so distant future, the fight to win over Muslims will move from battle and oil fields to digital domains.
Those with aspirations for becoming a global caliph will be busy amassing Facebook friends and Twitter followers. A self-professed caliph near the border of Syria and Iraq and a self-proclaimed Ameer-ul-Momineen in the Pashtun dominated areas of Afghanistan will be the first to compete for a larger number of online followers.
It does not matter how unsocial one may be, social media, at least for now, is serving the communication needs of Jihadists and other extremists.
As the technology continues to evolve, one hopes that the Web 3.0 tools will arrive with automated filters to expose bigots and to make it harder to exploit the naivety of the youth.
Source: